Alongside Ryan Feng, I am co-organizing a reading group for Autonomous Vehicle (AV) Safety and Security. This is hosted in the CSE Department at the University of Michigan, but anyone who is able to make it in-person is welcome to join.
What is AV “Safety” and “Security”?
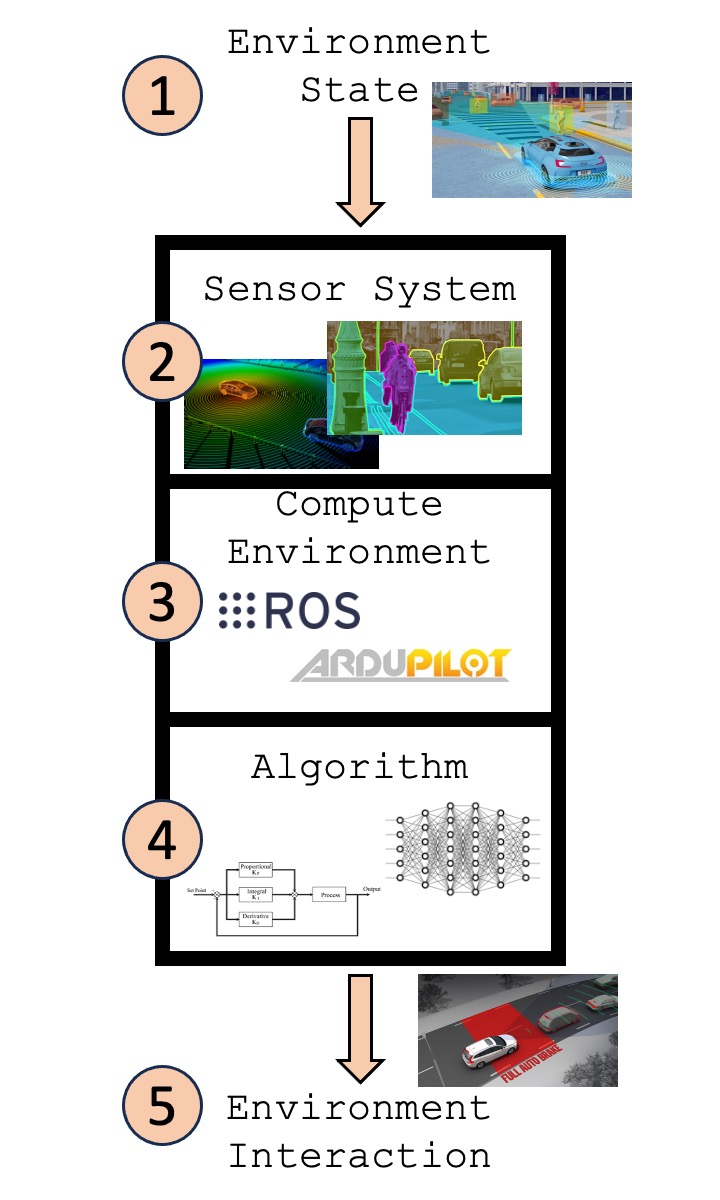
- Major components to AV safety and security.
To guide this question, take a look at the figure. During the process of AV operation there are five general components that we observe having important safety/security concerns that the literature focuses on.
This taxonomy is not meant to be complete, but rather a guide for our reading group; there are definitely a few missing components during our simplification. If there are topics related to AV safety and security that don’t fall into our definition, please introduce them during our reading group meetings!
Environment State
The state of the environment has sensitive and private information. Since autonomous vehicles have diverse perception systems, this information is collected and stored locally/remotely. This data maybe be used to diminish upon one’s ability to exist in public without being spied on.
Sensor System
Failures and attacks may directly compromise the sensor system’s ability to deliver correct data. Perception fault detection and mitigation is thus an active area of research. Downstream impact on the control of the vehicle is an important area of interest here.
Compute Environment
Autonomous vehicle middleware, such as ROS or ArduPilot, facilitates the communication and management of important sensor data and control choices. If the middleware is compromised or incorrect, this can have dangerous effects on the AV’s control.
Algorithm
AVs have a few types of control algorithms. Some have bounded known error that they can have given a set of assumptions, but faulty sensor data may cause violations of these assumptions. Likewise, deep neural networks may have distribution shifts due to various environmental factors. These issues with the algorithms may cause control failure.
Environment Interaction
There are physical constraints that the AV must operation within as it traverses its environment (e.g., hard deadlines, social patterns, reacting to context). An adversary or fault can cause the AV to violate the constraints of the environment and cause dangerous outcomes.
Goals and Expectations
-
This reading group will focus more on the discussion of the chosen papers, so we expect each attendee to read/skim the paper enough to have a basic understanding.
-
Each week a volunteer will lead the discussion for a paper of their choosing. The volunteer may use some pre-existing slide deck from a conference, but no expectation to make their own slides. The volunteer may give a brief (~15 min.) summary of the paper, but the majority of the time should be for open discussion.
-
During the last few minutes, the volunteer will work with the group to summarize the takeaways from the discussion. The idea is to have something to “chew on” mentally after we leave the meeting. To make this easier, one participant may volunteer to take notes during the meeting so that we can share them with the group (and with permission we may share them publicly if we find them to be a useful resource).
-
Finally, the primary goal of this reading group is to gain exposure to a wide range of topics related to AV safety and security. If an interesting paper is not strictly covered by our above definition yet seems related, we encourage the volunteer to introduce the paper. It may be beneficial to everyone to see something outside of the norm.
When? Where? Email List?
Fridays from 2:00 PM to 3:00 PM in BBB 2725.
Join the MCommunity group here to receive emails.
Upcoming and Past Schedule
Winter 2024 Schedule
Jinrang Jia, et al. MonoUNI: A Unified Vehicle and Infrastructure-side Monocular 3D Object Detection Network with Sufficient Depth Clues, in the Proceedings of the 37th Conference on Neural Information Processing Systems (NeurIPS '23), 2023.
R. Spencer Hallyburton, et al. A Multi-Agent Security Testbed for the Analysis of Attacks and Defenses in Collaborative Sensor Fusion, in the Proceedings of the 2nd ISOC Symposium on Vehicle Security and Privacy (VehicleSec '24), 2024.
Yanmao Man, et al. That Person Moves Like A Car: Misclassification Attack Detection for Autonomous Systems Using Spatiotemporal Consistency, in the Proceedings of the 32nd USENIX Security Symposium (USENIX '23), 2023.
Wei Wang, et al. I Can See the Light: Attacks on Autonomous Vehicles Using Invisible Lights, in the Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security (CCS '21), 2021.
Fall 2023 Schedule
Rachel Luo, et al. Sample-Efficient Safety Assurances Using Conformal Prediction, in the Proceedings of the 15th International Workshop on the Algorithmic Foundations of Robotics (WAFR '22), 2022.
Ruoyu Song, et al. Discovering Adversarial Driving Maneuvers against Autonomous Vehicles, in the Proceedings of the 32nd USENIX Security Symposium (USENIX Security '23), 2023.
Chulin Xie, et al. Privacy of Autonomous Vehicles: Risks, Protection Methods, and Future Directions, in arXiv, 2022.
R. Spencer Hallyburton, et al. Partial-Information, Longitudinal Cyber Attacks on LiDAR in Autonomous Vehicles, in arXiv, 2023.
Sabbir Ahmed, et al. DFR-TSD: A Deep Learning Based Framework for Robust Traffic Sign Detection Under Challenging Weather Conditions, IEEE Trans. on Intelligent Transportation Systems, 2022.
Yulong Cao, et al. Invisible for Both Camera and LiDAR: Security of Multi-Sensor Fusion Based Perception in Autonomous Driving Under Physical-World Attacks, in the Proceedings of the 2021 IEEE Symposium on Security and Privacy (Oakland '21), 2021.
Jinlong Li, et al. Domain Adaptive Object Detection for Autonomous Driving Under Foggy Weather, in the Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision (WACV '23), 2023.
Zhijian Liu, Haotian Tang, et al. BEVFusion: Multi-Task Multi-Sensor Fusion with Unified Bird's-Eye View Representation, in the Proceedings of the 2023 IEEE International Conference on Robotics and Automation (ICRA '23), 2023.
Ionel Gog, et al. D3: A Dynamic Deadline-Driven Approach for Building Autonomous Vehicles, in the Proceedings of the Seventeenth European Conference on Computer Systems (EuroSys '22), 2022.
Paper List
Some papers may fit into multiple categories. We place them in the main area we feel their contributions focus on.
① Environmental Privacy
Chulin Xie, et al. Privacy of Autonomous Vehicles: Risks, Protection Methods, and Future Directions. arXiv:2209.04022, 2022.
Dorothy J. Glancy. Privacy in Autonomous Vehicles. Santa Clara Law Review, 2012.
Luis F. Alvarez León. Eyes on the Road: Surveillance Logics in the Autonomous Vehicle Economy. Surveillance & Society, 2019.
② Sensor System Attacks/Failures
Yulong Cao, et al. You Can't See Me: Physical Removal Attacks on LiDAR-based Autonomous Vehicles Driving Frameworks. in the Proceedings of the 32nd USENIX Security Symposium (Security '23), 2023.
Qifan Xiao, et al. Exorcising 'Wraith': Protecting LiDAR-based Object Detector in Automated Driving System from Appearing Attacks. in the Proceedings of the 32nd USENIX Security Symposium (Security '23), 2023.
③ Computing Environment Integrity
Hyungsub Kim, et al. PGFUZZ: Policy-Guided Fuzzing for Robotic Vehicles. in the Proceedings of the Network and Distributed Systems Security Symposium 2021 (NDSS '21), 2021.
Yunpeng Luo, et al. Poster: Towards Complete Computation Graph Generation for Security Assessment of ROS Applications. in the Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security (CCS '22), 2022.
Bernhard Dieber, et al. Application-Level Security for ROS-Based Applications. in the Proceedings of the 2016 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS '16), 2016.
R. Spencer Hallyburton, et al. Partial-Information, Longitudinal Cyber Attacks on LiDAR in Autonomous Vehicles. arXiv:2303.03470, 2023.
④ Robustness of Control/Decision Algorithms
Maximilian Jaritz, et al. xMUDA: Cross-Modal Unsupervised Domain Adaptation for 3D Semantic Segmentation. in the Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR '20), 2020.
Abhinav Valada, et al. AdapNet: Adaptive Semantic Segmentation in Adverse Environmental Conditions. in the Proceedings of the 2017 IEEE International Conference on Robotics and Automation (ICRA '17), 2017.
Oier Mees, et al. Choosing Smartly: Adaptive Multimodal Fusion for Object Detection in Changing Environments. in the Proceedings of the 2016 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS '16), 2016.
Jinlong Li, et al. Domain Adaptive Object Detection for Autonomous Driving Under Foggy Weather. in the Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision (WACV '23), 2023.
Dogancan Temel, et al. CURE-TSR: Challenging Unreal and Real Environments for Traffic Sign Recognition. Neural Information Processing Systems (NeurIPS) Workshop on Machine Learning for Intelligent Transportation Systems (MLITS), 2017.
Sabbir Ahmed, et al. DFR-TSD: A Deep Learning Based Framework for Robust Traffic Sign Detection Under Challenging Weather Conditions. IEEE Transactions on Intelligent Transportation Systems, 2022.
⑤ Environmental Constraints/Impact
Yanmao Man, et al. That Person Moves Like A Car: Misclassification Attack Detection for Autonomous Systems Using Spatiotemporal Consistency. in the Proceedings of the 32nd USENIX Security Symposium (Security '23), 2023.
